Security of Manageability vs.
Manageability of Security (Jeff Bohren)
-
Security of Manageability - The security of the Manageability Provider and the underlying communications protocols. How are the management requests authenticated? How are management requests authorized and audited?
-
Manageability of Security - What security information on the managed resource can be managed by the Manageability Provider. How is this information presented to the Manager. In MOWS, there is the specific use case of managing the configuration of the Web Service Security infrastructure for that web service (among other things).
Security Considerations
between Manager and Manageability Provider (Andreas
Dharmawan)
-
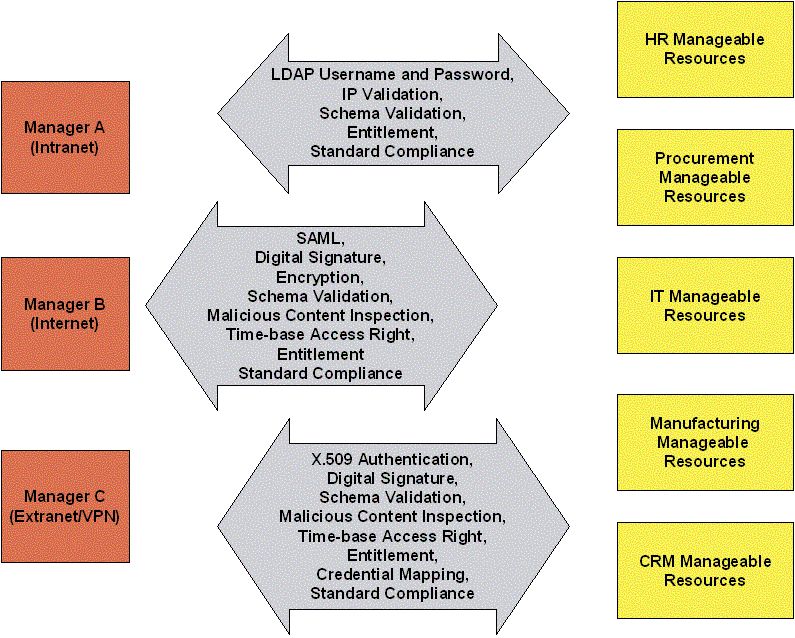
In an enterprise there will be many manageability resources that belong to many different departments.
-
Multiple managers may involve in the management of different resources from different departments.
-
Managers may be interacting with the manageability providers from the intranet, extranet, and intranet.
-
Samples of security considerations:
-
Authentication and Authorization
-
Confidentiality
-
Non-repudiation
-
Schema Validation
-
Standard Compliance
-
The same manager may be required to use different kinds of credentials when accessing a manageable provider based on whether s/he in the intranet, extranet, or internet.
Possible Categories of
Manageability of Security (Jeff Bohren)
-
Configuration:
Transport level authentication settings
PKI Info (server cert, trusted CAs, CRLs)
TLS Configuration
HTTP restrictions (allowed verbs, etc)
SOAP specific security settings
-
Metrics:
Successful Authentications (total, per time period, etc)
Failed Authentications
Successful Authorizations
Failed Authorizations
-
Notifications:
Failed Authentications
Failed Authorizations
-
Policies:
Access control rules
Privacy vs. Confidentiality vs.
Authentication and Authorization (Mark Ellison, Hal
Lockhart)
-
It is now conventional to refer to this requirement (encryption) as "confidentiality" rather than "privacy". The reason is that privacy is normally used to indicate the variety of concerns and mechanisms required to assure individual's security.
Many security mechanisms, e.g. encryption, access control may have privacy as one of its motivations, but privacy requirements may also involve unique requirements and technologies.
MUWS Security Requirements
Recap
-
•[SEC.001] The Manageability Interface MUST enable secure management, as dictated by the threats of the environment. This includes (but is not limited to) support for the functionality described in the sub-requirements, SEC.001.1-6.
-
[SEC.001.1] The Manageability Interface SHOULD support having the manager authenticate the manageable resource.
-
[SEC.001.2] The Manageability Interface SHOULD support having the manageable resource authenticate the manager.
-
[SEC.001.3] The Manageability Interface SHOULD support an underlying mechanism that guarantees the integrity of the messages exchanged.
-
[SEC 001.4] The Manageability Interface SHOULD support an underlying mechanism that guarantees the confidentiality of the messages exchanged.
-
[SEC 001.5] The Manageability Interface SHOULD not preclude establishing, using, and managing trust relationships.
-
[SEC.001.6] The Manageability Interface SHOULD support access control (such as distinguishing between the ability to view and the ability to change) for management information, operations and event notifications at appropriate granularity. Access SHOULD be controllable by role (the security mechanism being used will determine what “role” means). For example, an internal manager should have greater control than a manager being run by a partner.
-
[SEC.002] The Manageability Interface MUST be NAT and firewall "friendly", meaning that the interface MUST NOT require additional support in NAT and firewall products, and that sufficient information MUST be provided for a firewall proxy to inspect the management messages.
-
[SEC.003] The Manageability Interface MUST not increase security risks or enlarge security exposures.
-
[SEC.004] The Manageability Interface MUST allow a self-contained, fallback security model, for use when the security infrastructure is not available.
-
[SEC.005] The Manageability Interface MUST be able to be used to manage a Security Infrastructure
-
[SEC.005.1] The Manageability Interface MUST allow operational capabilities on security features (e.g., enable, disable). Security configuration SHOULD only be allowed via the Manageability Interface if appropriate access controls are in place.