Date: Wednesday, May 11, 2016 at 7:11 PM
To: "Maxwell, Kyle" <kmaxwell@verisign.com>, "Jordan, Bret" <bret.jordan@bluecoat.com>, "cti-stix@lists.oasis-open.org" <cti-stix@lists.oasis-open.org>
Subject: Re: [cti-stix] Campaign Mini-Group Working Session
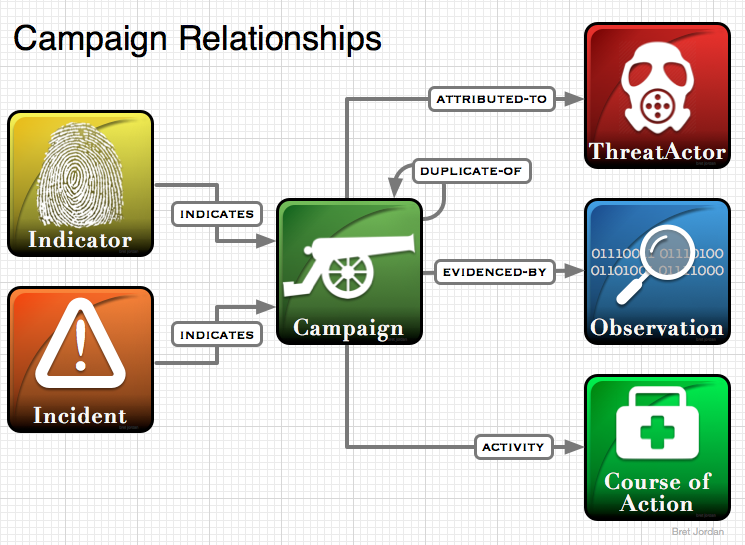
- If it often helpful to associate a specific campaign with other campaigns, but not duplicate ones. Campaigns, especially by nation states often reoccur on a periodic basis and are not one time instances. A re-occurring campaign is NOT a duplicate and the fact that it re-occurs is a key aspect of intelligence about a campaign
- Campaigns generally leverage TTPs since the TTP characterizes how the campaign evolves/is played out, who it targets, what types of exploits it utilizes, identifies patterns or sequences of attack steps, etc. So a campaign need to have a reference to TTPs that are leveraged or related to the campaign. Remember it may not be possible to identify the threat actor(s) to which the campaign is able to be attributed to and yet characterization of how the campaign ‘functions’ are identifiable, so you can’t rely upon getting to the TTPs of the campaign via attribution to a threat actor(s).
- Characterizing a campaign requires relationships from the campaign to the indicators used to detect the campaign, not observations, and from the campaign to incidents that were reportedly as a result of the campaign. Clearly there inverse relationship between campaign, indicator, and incident is also true. But having only a relationship from those items to the campaign makes it very difficult to describe a characterization of the campaign is a straightforward manner.
- There is only an indirect relationship between a Campaign and one or more corresponding Courses of Actions. Its indirect because you can not directly mediate a campaign, only the exploits that are leveraged by a campaign. The exploits that are targeted by a campaign are defined through the use of TTPs, thus the relationship is Campaign—> TTP —> Exploit Target. I believe there is confusion about the purpose of the Activity property and the use of Courses of Action as COAs are meant to represent corrective actions and preventative steps (remediation or countermeasures). The activity property is used to capture just generic actions that is meant to be extended.
Date: Wednesday, May 11, 2016 at 1:13 PM
To: "Jordan, Bret" <bret.jordan@bluecoat.com>, "cti-stix@lists.oasis-open.org" <cti-stix@lists.oasis-open.org>
Subject: RE: [cti-stix] Campaign Mini-Group Working Session
Resent-From: <Paul.Patrick@FireEye.com>
I should be on the call, but if not, here are some additional relationships to think about:
- Campaign targets a Victim (organization or vertical)
- If ThreatActor and ThreatGroup are not identical, Campaigns may be attributed to the latter
- Campaign uses a TTP
iDefense Senior Analyst
From:cti-stix@lists.oasis-open.org [cti-stix@lists.oasis-open.org] on behalf of Jordan, Bret [bret.jordan@bluecoat.com]
Sent: Tuesday, May 10, 2016 19:20
To: cti-stix@lists.oasis-open.org
Subject: [cti-stix] Campaign Mini-Group Working Session
For our discussion tomorrow on campaigns, here is a diagram I put together for Campaign Relationships in STIX 2.0. This should help us better identify and understand where things are missing.
[cti-stix] Campaign Mini-Group Working Session
Scheduled: May 11, 2016, 13:00 to 14:00
Location: Online Meeting
Invitees: Jordan, Bret, cti-stix@lists.oasis-open.org
All,
The campaign mini-group wants to have a discussion to finalize their proposal to the broader SC. No need to join unless you want to influence this early stage development on the campaign TLO.
John
.........................................................................................................................................
Join online meeting <https://meet.mitre.org/jwunder/HRTBLWS0>
https://meet.mitre.org/jwunder/HRTBLWS0
Join by Phone
+1 (781) 271-2020
+1 (703) 983-2020
Find a local number <https://dialin.mitre.org>
Conference ID: 7622872
Forgot your dial-in PIN? <https://dialin.mitre.org> | First online meeting? <http://r.office.microsoft.com/r/rlidOC10?clid=1033&p1=4&p2=1041&pc=oc&ver=4&subver=0&bld=7185&bldver=0>
.........................................................................................................................................
Thanks,
Bret
Bret Jordan CISSPDirector of Security Architecture and Standards | Office of the CTOBlue Coat SystemsPGP Fingerprint: 63B4 FC53 680A 6B7D 1447 F2C0 74F8 ACAE 7415 0050"Without cryptography vihv vivc ce xhrnrw, however, the only thing that can not be unscrambled is an egg."