Hi!,
How does one map the reliability to the score as well ?, there are two components to the admiralty code ?, we could almost use a restricted keyword set to control
the various classifications, however we do need to take into account that we may not always have the information we need to construct the admiralty code (ie. threat data re-shared, obtained via other sources, and so forth).
We also run into the complication that person A might think source Z is really good, whilst B thinks source Z is not so good.
Regards,
Dean
From: cti@lists.oasis-open.org [mailto:cti@lists.oasis-open.org]
On Behalf Of Jason Keirstead
Sent: Friday, 9 September 2016 7:11 AM
To: Patrick Maroney
Cc: cti@lists.oasis-open.org; cti-stix@lists.oasis-open.org; Dave Cridland; JE; Terry MacDonald
Subject: Re: [cti] Re: [cti-stix] MISP Taxonomies [Was: CTI Brussels F2F Meeting...RSVP deadline 5 September]
I was kind of thinking along the lines of this mapping
- Confidence in STIX is defined as a value from 0 - 100 where "-1" is a reserved value mapped to "unknown"
- Admirality scale then maps to
F - -1
E - 20
D - 40
C - 60
B - 80
A - 100
-
Jason Keirstead
STSM, Product Architect, Security Intelligence, IBM Security Systems
www.ibm.com/security |
www.securityintelligence.com
Without data, all you are is just another person with an opinion - Unknown
![]() Patrick
Maroney ---09/08/2016 10:58:25 PM---Re: "I very much like the idea of adding support for the MISP taxonomies..,, KEWL! ...but I still
Patrick
Maroney ---09/08/2016 10:58:25 PM---Re: "I very much like the idea of adding support for the MISP taxonomies..,, KEWL! ...but I still
From: Patrick Maroney <Pmaroney@Specere.org>
To: Jason Keirstead/CanEast/IBM@IBMCA
Cc: "cti@lists.oasis-open.org" <cti@lists.oasis-open.org>, "cti-stix@lists.oasis-open.org"
<cti-stix@lists.oasis-open.org>, "Dave Cridland" <dave.cridland@surevine.com>, JE <je@cybersecurityscout.eu>, "Terry
MacDonald" <terry.macdonald@cosive.com>
Date: 09/08/2016 10:58 PM
Subject: [cti] Re: [cti-stix] MISP Taxonomies [Was: CTI Brussels F2F Meeting...RSVP deadline 5 September]
Sent by: <cti@lists.oasis-open.org>
Re: "I very much like the idea of adding support for the MISP taxonomies..,, KEWL!
...but I still think that confidence should be a numerical value.
I would like to see a way that the admiralty scale taxonomy can be mapped to a numerical equivalent. That way if someone wants to use a different taxonomy because the admiralty scale is either too broad or too narrow, they are
free to do so, because we are not directly mandating it be used."
[Musings: ]
One approach would be to simply define and publish a MISP taxonomy with whatever numeric scale(s) you wish (presumably consensus driven). I've seen good arguments for 1-5, 1-100, and even "0.000" to "1.0" for probability based
metrics. Same sort of arguments for "H", "M", "L" Confidence vs. Numeric.
Note that I'm not arguing for one or the other, I'm arguing for flexibility if we can manage same with a very well defined, non-subjective, set of conventions/rules.
[Thinking outside the litter box:]
Transformations of data from one representation to another is going to be required in many common scenarios. For example, If someone has an internal COTs Trouble Ticketing System X that uses "H", "M", "L" and the data for that
parameter comes in a numeric 1-100 form, your going to have to map/transform the data sooner or later. If we instead accept this as a fact of life and frame out a central transformation architecture, we can provide a consistent framework and repeatable processes
all can leverage.
I have some concepts I want to propose (when they're flushed out and documented). The basic concept is to add a series of Transformation, Tokenization, Redaction, Testing, etc. services to the TAXII Architecture Specification.
These functions could be applied to data transiting a TAXII "Transport Only" Gateway, or run as REST Services on a TAXII Repo/TAXII EndPoint.
I'll use the multi ISAC collaboration through a third party like the National Council of ISACs (NCI) as an example. Each ISAC has it's own variants on rules regarding TLP, data handling/marking. ISAC A requires that data it sends
to other ISACs via NCI is marked one TLP Level higher once it's leaves the ISAC A's COT (Community of Trust). This transformation rule would be applied to ISAC A's Central COT TAXII Gateway that inter-exchanges data with NCI and other external parties.
For example, If there was a convention that all individual ISAC TLP marking get a "bump" when transiting the NCI central TAXII Services, that would be applied centrally. Similarly NCI acting as a central trusted third party may
need to Arbitrate variants between ISACs on rules regarding TLP, data handling/marking. By providing a modular TAXII Services architecture for integrating a series of Transformation, Tokenization, Redaction, Testing, etc. services into the TAXII Transit Gateways,
TAXII Repositories, and TAXII End-Points we can do some very powerful things, including addressing many of the concerns/requirements we've been discussing.
By integrating these functions into the fabric of "Our Thing" (in the TAXII Services Framework) we can crowd source the development of shared solutions to common problems and apply them consistency across the ecosystem.
I've been playing around with this to test/validate the Tokenization Concepts proposed to the Community
(https://www.linkedin.com/pulse/case-automated-cyber-threat-intelligence-tokenization-patrick-maroney).
It probably sounds more complex than it is.
However, I won't ready to formally "pitch" this concept until We can test against reference implementations once we get the Next Generation RESTful TAXII servers up and running.
Patrick Maroney
President
Integrated Networking Technologies, Inc.
Desk: (856)983-0001
Cell: (609)841-5104
Email: pmaroney@specere.org
_____________________________
From: Jason Keirstead <jason.keirstead@ca.ibm.com>
Sent: Thursday, September 8, 2016 3:39 PM
Subject: Re: [cti-stix] MISP Taxonomies [Was: CTI Brussels F2F Meeting...RSVP deadline 5 September]
To: Patrick Maroney <pmaroney@specere.org>
Cc: <cti@lists.oasis-open.org>, <cti-stix@lists.oasis-open.org>,
Dave Cridland <dave.cridland@surevine.com>, JE <je@cybersecurityscout.eu>,
Terry MacDonald <terry.macdonald@cosive.com>
I very much like the idea of adding support for the MISP taxonomies, but I still think that confidence should be a numerical value.
I would like to see a way that the admiralty scale taxonomy can be mapped to a numerical equivalent. That way if someone wants to use a different taxonomy because the admiralty scale is either too broad or too narrow, they are free to do so, because we are
not directly mandating it be used.
-
Jason Keirstead
STSM, Product Architect, Security Intelligence, IBM Security Systems
www.ibm.com/security |
www.securityintelligence.com
Without data, all you are is just another person with an opinion - Unknown
![]() Patrick
Maroney ---09/08/2016 01:29:55 PM---Good discussion folks. In support of the concepts expressed here, I'd like to raise the topic of su
Patrick
Maroney ---09/08/2016 01:29:55 PM---Good discussion folks. In support of the concepts expressed here, I'd like to raise the topic of su
From: Patrick Maroney <Pmaroney@Specere.org>
To: Dave Cridland <dave.cridland@surevine.com>, JE <je@cybersecurityscout.eu>
Cc: "cti@lists.oasis-open.org" <cti@lists.oasis-open.org>, "cti-stix@lists.oasis-open.org" <cti-stix@lists.oasis-open.org>,
"Terry MacDonald" <terry.macdonald@cosive.com>
Date: 09/08/2016 01:29 PM
Subject: [cti-stix] MISP Taxonomies [Was: CTI Brussels F2F Meeting...RSVP deadline 5 September]
Sent by: <cti-stix@lists.oasis-open.org>
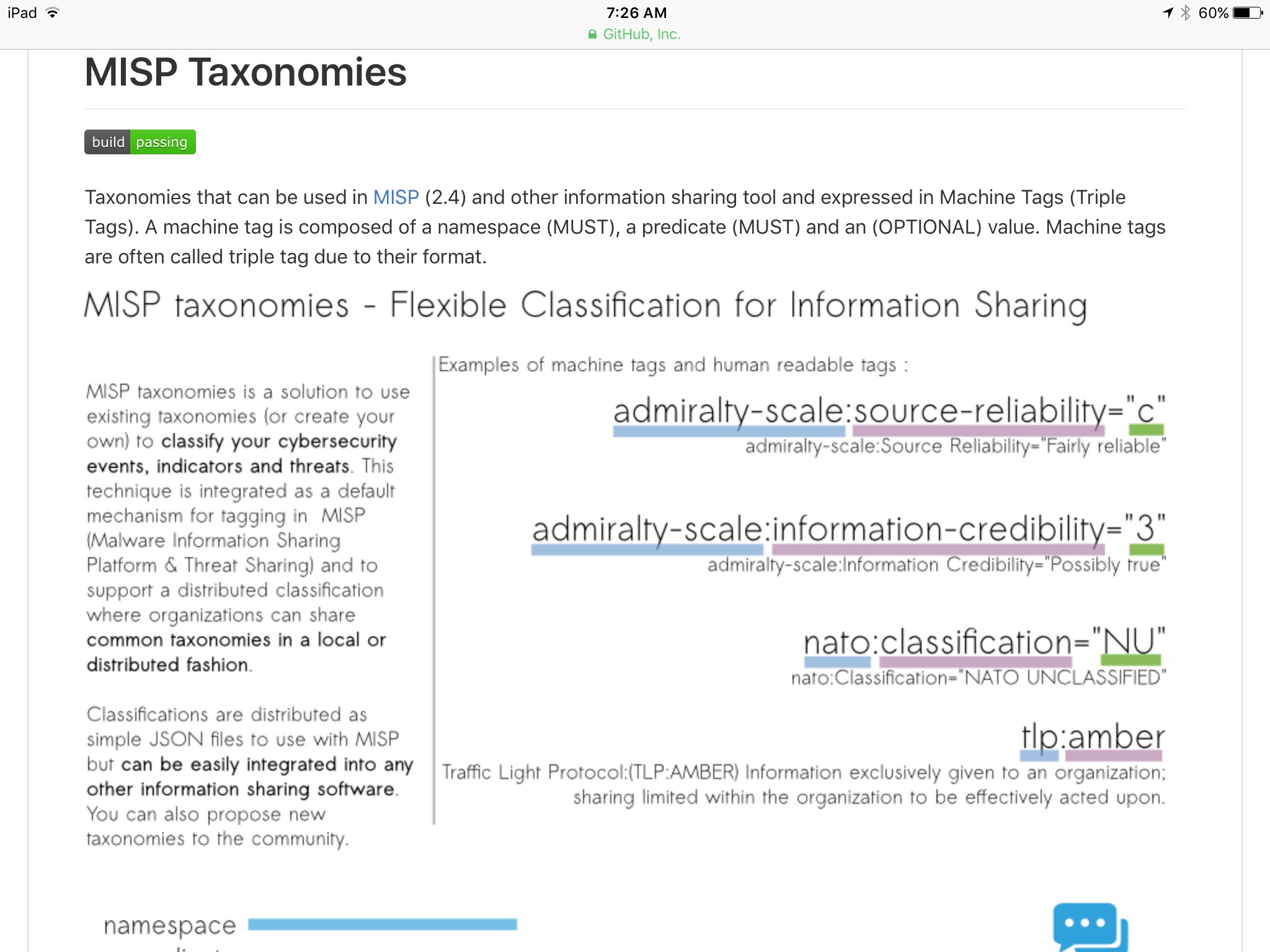
Good discussion folks. In support of the concepts expressed here, I'd like to raise the topic of supporting the MISP Taxonomy format and the public repository of Taxonomies and format for consideration.
https://github.com/MISP/misp-taxonomies
Alexandre Dulaunoy has cleared up concerns raised regarding licensing, so we can assess on the technical merits.
Patrick Maroney
President
Integrated Networking Technologies, Inc.
Desk: (856)983-0001
Cell: (609)841-5104
Email: pmaroney@specere.org
From:
cti@lists.oasis-open.org <cti@lists.oasis-open.org>
on behalf of Dave Cridland <dave.cridland@surevine.com>
Sent: Thursday, September 8, 2016 4:13:31 AM
To: JE
Cc: cti-stix@lists.oasis-open.org;
cti@lists.oasis-open.org; Terry MacDonald
Subject: RE: [cti] CTI Brussels F2F Meeting...RSVP deadline 5 September
There's two approaches, both already existing, which can help with this. Firstly, a common, shared policy (and just as important, commonly understood semantics). The FIRST IEP work is along these lines.
Secondly, real security label/classification/policy systems allow one policy to be translated to another, as long as the semantics can be mapped. These systems exist already, and are specified in a slew of documents include
SDN.801(c), X.841, and so on.
Obviously these two are complementary - if there are lots of common semantics in organisation's policies, it makes it easy to express handling requirements, and the existing label specs allow each organization to have their
own policy which they can develop independently.
But all this is already handled by STIX - it's just payload data to STIX and TAXII.
Dave.
On 8 Sep 2016 09:29, "JE" <je@cybersecurityscout.eu> wrote:
Hi Terry,
Sorry I was not clear enough in my suggestion and putting it into context… we’re on the same page, there are currently discussions going on in some communities to
extend TLP scheme (proprietary) by validation information and within some schemes used in intel (usually not public / publicly known) this is already existing as part of their schemes. Unfortunately proprietary approaches have their issues when trying to make
it work outside the origin.
To enable a true policy-based management, enforcement, priority handling etc. it’s vital to have a standard on assigning & processing level of confidence, trust
in source and possibly validation by analyst as well. Some of the European ISACs I know handle this by reserving some classification levels for members and assign trust-by-default but of course this does not scale beyond limited community nor is it a feasible
way to apply it on granular objects.
Cheers from Brussels,
Joerg
From:
cti@lists.oasis-open.org [mailto:cti@lists.oasis-open.org]On
Behalf Of Terry MacDonald
Sent: Wednesday, September 7, 2016 21:11
To: JE <je@cybersecurityscout.eu>
Cc: cti-stix@lists.oasis-open.org;cti@lists.oasis-open.org;
Thompson, Dean <Dean.Thompson@anz.com>
Subject: RE: [cti] CTI Brussels F2F Meeting...RSVP deadline 5 September
Hi Joerg,
I wasn't meaning information handling or policy management at all, as this is already supported via the object level data marking or granular date marking in STIX 2.0.
I was definitely meaning a way of describing confidence that the threat intelligence is correct, and confidence that the person who told you the threat intelligence gets it right. We had that functionality
in STIX 1.x series, and we've lost it in STIX 2.0.
We need to add it back on as part of STIX 2.1.
Cheers
Terry MacDonald
Cosive
On 7/09/2016 10:25 PM, "JE" <je@cybersecurityscout.eu> wrote:
Dear All,
I fully support this – having built some ISACs in industry as well as GOV classification/labeling is usually a “top 5 “ issue … if not at the time of initial set-up
than usually later when information from different sources is to be shared and utilized. This might not be a primary issue from vendor side (although it should be as most TI is not under monolithic policy/license rights but compiled) it is definitely an issue
from user perspective to handle, distribute and leverage TI properly,
Some of the commercially available systems on the market implement labeling/label-based-handling in a proprietary way as current information models/standards do
not foresee this. If you e.g. look at OTRS (not a STIX/TAXI implementation but wide used for Service + Incident Mgt), actually an open source system but during the evolution also included labeling and handling according to this. No matter if e.g. TLP or other
schemes are applied I strongly suggest to at least include the option to label objects and though enable/apply/enforce policy-based information exchange and handling.
Sunny greetings from Berlin & looking forward meeting you guys f2f on later Wednesday evening in Brussels,
Joerg
From:
cti@lists.oasis-open.org [mailto:cti@lists.oasis-open.org]On
Behalf Of Thompson, Dean
Sent: Wednesday, September 7, 2016 03:06
To: 'Terry MacDonald' <terry.macdonald@cosive.com>;
'cti@lists.oasis-open.org' <cti@lists.oasis-open.org>;
'cti-stix@lists.oasis-open.org' <cti-stix@lists.oasis-open.org>
Subject: RE: [cti] CTI Brussels F2F Meeting...RSVP deadline 5 September
Hi!,
Can I add my voice in here as well and say that “Confidence” and also having an “Opinion” about Threat Intelligence is very important and is a concept
that we use quite heavily when we are exchanging threat intelligence with other financial organisations and dealing with threat data that comes in via 3rd parties and intelligence sources.
Can we please ensure that this is included in the agenda and discussed at the meeting ?
Regards,
Dean
From:
cti@lists.oasis-open.org [mailto:cti@lists.oasis-open.org]On
Behalf Of Terry MacDonald
Sent: Wednesday, 7 September 2016 8:18 AM
To: cti@lists.oasis-open.org;cti-stix@lists.oasis-open.org
Subject: Re: [cti] CTI Brussels F2F Meeting...RSVP deadline 5 September
Please say that we are including confidence and opinion object in STIX 2.1 candidate smackdown agenda item at the F2F.
We just can't treat everything that people send out as the absolute truth as we do in STIX 2.0. There is a reason things like the admiralty code were developed.... and that's because threat intelligence
is always someone's opinion.We need a way for the consumer to understand how confident the producer is in the threat intelligence they are sending. It's up to the consumer to determine if they believe that its the truth, and they need various ways to determine
this. That's a ton easier if the person who sent the threat intelligence to you tells you how much they trust the intelligence and trust the source of the intelligence with some form of confidence field.....
I really, really believe this is critical for STIX to work properly, and it was something that made it possible for STIX to automatically be pushed out to the different security tools within an organization
(e.g. high confidence DNS to the DNS RPZ block, low confidence to the alerting on the passive DNS).
These are so easy to add to STIX, we would be remiss to skip it.
Cheers
Terry MacDonald| Chief Product Officer
![]()
On Fri, Sep 2, 2016 at 8:53 AM, Jane Harnad <jharnad@oasis-open.org>
wrote:
Dear CTI Members,
The CTI TC F2F meeting is scheduled for Wednesday, 7 September at the Thon EU Hotel,
Germany Room. Lunch and refreshments will be provided by OASIS. A headcount is needed ASAP. Below is a list of individuals that replied to the last RSVP request. If you don't see your name and do plan to participate in either the F2F meeting or group dinner,
please send your RSVP no later than 5 September.
Remote access is available to TC members unable to attend in person.
Login details are:
https://global.gotomeeting.com/join/978573765
You can also dial in using your phone.
United States (Toll-free): 1 866 899 4679
United States
+1 (646) 749-3117
Access Code: 978-573-765
Proposed agenda is attached.
Details on group dinner option: CTI members are invited to sign up to attend a group
dinner on Wednesday evening after the F2F. Family members and/or guests traveling along with you are also invited to join us. This is not a hosted dinner, so each participant (and their guests) will be responsible for covering the costs associated with their
dinner. Please be sure to confirm the number of guests.
Thanks so much and we look forward to seeing you all in Brussels!
Regards, Jane
**F2F/Dinner Attendees
|
Bret Jordan |
|
|
Alexandre Dulaunoy |
|
|
Raymon van der Velde |
|
|
Ryusuke Masuoka |
|
|
Kazuo Noguchi |
|
|
Jason Keirstead |
|
|
Jerome Athias |
|
|
Allan Thomson |
|
|
Daniel Riedel |
|
|
John-Mark Gurney |
|
|
Carol Geyer |
|
|
Richard Struse |
|
|
Joerg Eschweiler |
|
|
Trey Darley |
|
|
Marko Dragoljevic |
|
|
Sergey Polzunov |
|
|
Aukjan van Belkum |
|
|
Wouter Bolsterlee |
|
|
Andras Iklody |
|
|
Mark Davidson |
|
|
Masato Terada |
|
--
Jane Harnad
Manager, Events
OASIS | Advancing open standards for the information society
+1.781.425.5073 x214 (Office)
http://www.oasis-open.org
Join OASIS at:
Borderless Cyber Europe8-9 Sept | Brussels
Borderless Cyber Asia1-2
Nov | Tokyo
---------------------------------------------------------------------
To unsubscribe from this mail list, you must leave the OASIS TC that
generates this mail. Follow this link to all your TCs in OASIS at:
https://www.oasis-open.org/apps/org/workgroup/portal/my_workgroups.php
This e-mail and any attachments to it (the "Communication") is, unless otherwise stated, confidential, may contain copyright material and is for the use only of the intended recipient. If you receive the Communication in error, please notify the sender immediately
by return e-mail, delete the Communication and the return e-mail, and do not read, copy, retransmit or otherwise deal with it. Any views expressed in the Communication are those of the individual sender only, unless expressly stated to be those of Australia
and New Zealand Banking Group Limited ABN 11 005 357 522, or any of its related entities including ANZ Bank New Zealand Limited (together "ANZ"). ANZ does not accept liability in connection with the integrity of or errors in the Communication, computer virus,
data corruption, interference or delay arising from or in respect of the Communication.
This e-mail and any attachments to it (the "Communication") is, unless otherwise stated, confidential, may contain copyright material and is for the use only of the intended recipient. If you receive the Communication in error, please notify the sender immediately by return e-mail, delete the Communication and the return e-mail, and do not read, copy, retransmit or otherwise deal with it. Any views expressed in the Communication are those of the individual sender only, unless expressly stated to be those of Australia and New Zealand Banking Group Limited ABN 11 005 357 522, or any of its related entities including ANZ Bank New Zealand Limited (together "ANZ"). ANZ does not accept liability in connection with the integrity of or errors in the Communication, computer virus, data corruption, interference or delay arising from or in respect of the Communication.