Please notes that for the CybOX object in Observed Data, I am just using a text description (hand-waving) at this point, since I have not yet written any code for CybOX data.
I would appreciate comments and feedback.
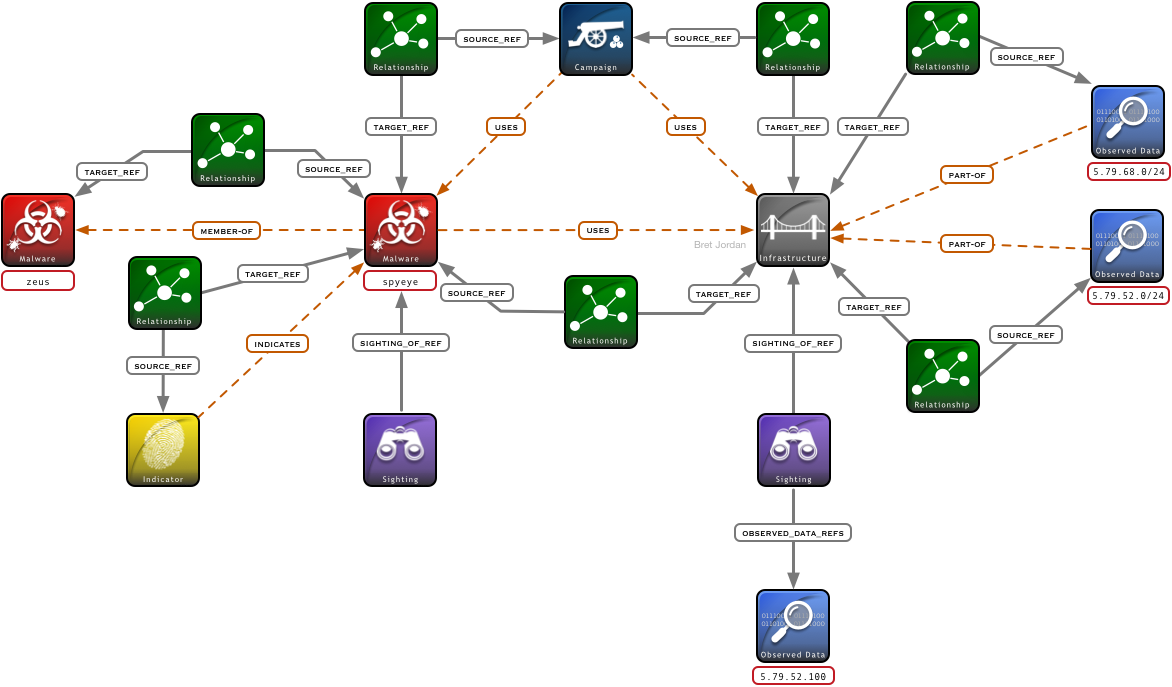
The main objects in this example are:
1) Campaign that uses both Malware and Infrastructure
2) Malware that is a "member-of" of a family of malware called Zeus
3) Observed Data for the Infrastructure 5.79.68.0/24 and a week later 5.79.52.0/24
4) A Sighting of the Malware SpyEye with no context
5) A Sighting of the Infrastructure with Observed Data context of a specific IP that was seen, 5.79.52.100
6) An Indicator for the MD5 hash of the SpyEye malware.

[12:19:38] saturn
[jordan]:/opt/go/src/github.com/freetaxii/libstix2/examples/bundle-> go run 01-bundle.go
{
"type": "bundle",
"id": "bundle--bc51f4a3-c53a-4037-bed5-fbc4d0092a51",
"spec_version": "2.0",
"campaigns": [
{
"type": "campaign",
"id": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "Bank Attack 2016",
"objective": "Compromise SWIFT system and steal money"
}
],
"indicators": [
{
"type": "indicator",
"id": "indicator--e38ee97c-af8b-487e-af1b-6f6f6257332b",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "Malware C2 Indicator 2016",
"description": "This indicator should detect the SpyEye malware by looking for this MD5 hash",
"pattern": "file-object:hashes.md5 = 84714c100d2dfc88629531f6456b8276"
}
],
"infrastructures": [
{
"type": "infrastructure",
"id": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "SpyEye Command and Control Servers",
"description": "These servers are located in a datacenter in the Netherlands and the IPs change on a weekly basis",
"kill_chain_phases": [
{
"kill_chain_name": "lockheed-martin-cyber-kill-chain",
"phase_name": "command-and-control"
}
],
"first_seen": "2016-09-01T00:00:01Z",
"region": "Europe",
"country": "NL"
}
],
"malware": [
{
"type": "malware",
"id": "malware--8f4c5264-617d-4175-9497-cff2913cd547",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"labels": [
"trojan",
"malware-family"
],
"name": "Zeus"
},
{
"type": "malware",
"id": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"labels": [
"trojan"
],
"name": "SpyEye",
"kill_chain_phases": [
{
"kill_chain_name": "lockheed-martin-cyber-kill-chain",
"phase_name": "command-and-control"
}
],
"filenames": [
"cleansweep.exe",
"spyeye2_exe",
"build_1_.exe"
],
"hashes": {
"md5": "84714c100d2dfc88629531f6456b8276",
"sha256": "861aa9c5ddcb5284e1ba4e5d7ebacfa297567c353446506ee4b4e39c84454b09"
},
"scan_data": [
{
"product": "avg",
"scanned": "2016-08-30T06:31:48Z",
"classification": "Generic16.BFGI"
},
{
"product": "avast",
"scanned": "2016-08-30T06:31:48Z",
"classification": "Win32:Downloader-NTU [PUP]"
}
]
}
],
"observed-data": [
{
"type": "observed-data",
"id": "observed-data--061addcc-71d6-4e96-95f3-3804b27b088d",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-01T00:00:01Z",
"last_observed": "2016-09-07T00:00:01Z",
"number_observed": 3,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.68.0/24"
},
{
"type": "observed-data",
"id": "observed-data--30f610cd-6ed6-49e1-944d-952e4b6bdc3b",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-07T00:00:01Z",
"last_observed": "2016-09-14T00:00:01Z",
"number_observed": 3,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.52.0/24"
},
{
"type": "observed-data",
"id": "observed-data--4abc8902-5ab7-4048-bbaa-36e223eb5bf2",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-07T00:00:01Z",
"last_observed": "2016-09-14T00:00:01Z",
"number_observed": 1,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.52.100"
}
],
"relationships": [
{
"type": "relationship",
"id": "relationship--e43290be-8e16-4ef0-97d2-43a28849638f",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "member-of",
"source_ref": "malware--8f4c5264-617d-4175-9497-cff2913cd547",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--9a2da770-9be8-4d3e-b0cf-11856ef7ca8d",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--3797f60e-9c87-4be1-ae12-789af3ad17a0",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--a96f71c8-2593-4705-8e8f-7f0d4a595d9a",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--5cc80e49-b50c-4c26-928f-8a55c925b208",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "indicates",
"source_ref": "indicator--e38ee97c-af8b-487e-af1b-6f6f6257332b",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--c8a8fc0d-36bd-4ef5-8a9e-f1ab68dac250",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "part-of",
"source_ref": "observed-data--061addcc-71d6-4e96-95f3-3804b27b088d",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--7bee75ef-d5c3-4b80-8f0c-4a3ea22c3bc2",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "part-of",
"source_ref": "observed-data--30f610cd-6ed6-49e1-944d-952e4b6bdc3b",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
}
],
"sightings": [
{
"type": "sighting",
"id": "sighting--a349cd2e-29a5-4a9e-b2d4-934d31fd7e7c",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_seen": "2016-09-01T00:00:01Z",
"last_seen": "2016-09-01T10:30:00Z",
"count": 3,
"sighting_of_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "sighting",
"id": "sighting--0f4a1dc5-0596-4262-8031-e25b707357c9",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_seen": "2016-09-01T00:00:01Z",
"last_seen": "2016-09-01T10:30:00Z",
"count": 10,
"sighting_of_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9",
"observed_data_ref": [
"observed-data--4abc8902-5ab7-4048-bbaa-36e223eb5bf2"
]
}
]
}
[jordan]:/opt/go/src/github.com/freetaxii/libstix2/examples/bundle-> go run 01-bundle.go
{
"type": "bundle",
"id": "bundle--bc51f4a3-c53a-4037-bed5-fbc4d0092a51",
"spec_version": "2.0",
"campaigns": [
{
"type": "campaign",
"id": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "Bank Attack 2016",
"objective": "Compromise SWIFT system and steal money"
}
],
"indicators": [
{
"type": "indicator",
"id": "indicator--e38ee97c-af8b-487e-af1b-6f6f6257332b",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "Malware C2 Indicator 2016",
"description": "This indicator should detect the SpyEye malware by looking for this MD5 hash",
"pattern": "file-object:hashes.md5 = 84714c100d2dfc88629531f6456b8276"
}
],
"infrastructures": [
{
"type": "infrastructure",
"id": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"name": "SpyEye Command and Control Servers",
"description": "These servers are located in a datacenter in the Netherlands and the IPs change on a weekly basis",
"kill_chain_phases": [
{
"kill_chain_name": "lockheed-martin-cyber-kill-chain",
"phase_name": "command-and-control"
}
],
"first_seen": "2016-09-01T00:00:01Z",
"region": "Europe",
"country": "NL"
}
],
"malware": [
{
"type": "malware",
"id": "malware--8f4c5264-617d-4175-9497-cff2913cd547",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"labels": [
"trojan",
"malware-family"
],
"name": "Zeus"
},
{
"type": "malware",
"id": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"labels": [
"trojan"
],
"name": "SpyEye",
"kill_chain_phases": [
{
"kill_chain_name": "lockheed-martin-cyber-kill-chain",
"phase_name": "command-and-control"
}
],
"filenames": [
"cleansweep.exe",
"spyeye2_exe",
"build_1_.exe"
],
"hashes": {
"md5": "84714c100d2dfc88629531f6456b8276",
"sha256": "861aa9c5ddcb5284e1ba4e5d7ebacfa297567c353446506ee4b4e39c84454b09"
},
"scan_data": [
{
"product": "avg",
"scanned": "2016-08-30T06:31:48Z",
"classification": "Generic16.BFGI"
},
{
"product": "avast",
"scanned": "2016-08-30T06:31:48Z",
"classification": "Win32:Downloader-NTU [PUP]"
}
]
}
],
"observed-data": [
{
"type": "observed-data",
"id": "observed-data--061addcc-71d6-4e96-95f3-3804b27b088d",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-01T00:00:01Z",
"last_observed": "2016-09-07T00:00:01Z",
"number_observed": 3,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.68.0/24"
},
{
"type": "observed-data",
"id": "observed-data--30f610cd-6ed6-49e1-944d-952e4b6bdc3b",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-07T00:00:01Z",
"last_observed": "2016-09-14T00:00:01Z",
"number_observed": 3,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.52.0/24"
},
{
"type": "observed-data",
"id": "observed-data--4abc8902-5ab7-4048-bbaa-36e223eb5bf2",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_observed": "2016-09-07T00:00:01Z",
"last_observed": "2016-09-14T00:00:01Z",
"number_observed": 1,
"cybox": "This will be a CybOX container object using the ipv4-addr object pointing to 5.79.52.100"
}
],
"relationships": [
{
"type": "relationship",
"id": "relationship--e43290be-8e16-4ef0-97d2-43a28849638f",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "member-of",
"source_ref": "malware--8f4c5264-617d-4175-9497-cff2913cd547",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--9a2da770-9be8-4d3e-b0cf-11856ef7ca8d",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--3797f60e-9c87-4be1-ae12-789af3ad17a0",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "campaign--afac1eee-0dd2-4656-8740-125d5fdb857c",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--a96f71c8-2593-4705-8e8f-7f0d4a595d9a",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "uses",
"source_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--5cc80e49-b50c-4c26-928f-8a55c925b208",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "indicates",
"source_ref": "indicator--e38ee97c-af8b-487e-af1b-6f6f6257332b",
"target_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "relationship",
"id": "relationship--c8a8fc0d-36bd-4ef5-8a9e-f1ab68dac250",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "part-of",
"source_ref": "observed-data--061addcc-71d6-4e96-95f3-3804b27b088d",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
},
{
"type": "relationship",
"id": "relationship--7bee75ef-d5c3-4b80-8f0c-4a3ea22c3bc2",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"relationship_type": "part-of",
"source_ref": "observed-data--30f610cd-6ed6-49e1-944d-952e4b6bdc3b",
"target_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9"
}
],
"sightings": [
{
"type": "sighting",
"id": "sighting--a349cd2e-29a5-4a9e-b2d4-934d31fd7e7c",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_seen": "2016-09-01T00:00:01Z",
"last_seen": "2016-09-01T10:30:00Z",
"count": 3,
"sighting_of_ref": "malware--29ea55ac-b907-4a34-b5ba-71fc93e2edb8"
},
{
"type": "sighting",
"id": "sighting--0f4a1dc5-0596-4262-8031-e25b707357c9",
"created": "2016-09-14T18:19:40Z",
"modified": "2016-09-14T18:19:40Z",
"version": 1,
"first_seen": "2016-09-01T00:00:01Z",
"last_seen": "2016-09-01T10:30:00Z",
"count": 10,
"sighting_of_ref": "infrastructure--7196a5e0-4db5-411b-aa5f-fac0a4f817b9",
"observed_data_ref": [
"observed-data--4abc8902-5ab7-4048-bbaa-36e223eb5bf2"
]
}
]
}
Thanks,
Bret
Bret Jordan CISSP
Director of Security Architecture and Standards | Office of the CTO
Blue Coat Systems
PGP Fingerprint: 63B4 FC53 680A 6B7D 1447 F2C0 74F8 ACAE 7415 0050
"Without cryptography vihv vivc ce xhrnrw, however, the only thing that can not be unscrambled is an egg."