On Mon, May 18, 2020 at 11:14 AM Andreas Kuehne <kuehne@trustable.de> wrote:
Hi Chet,
great! Would be a please or me to do a review!We (the Board Process Committee to be precise) is working on a process document now. I'm happy to share the working draft if you'd like to review it.
When you say "file it officially," do you mean that the TC has already developed the fix and that you want to announce it in one of the vulnerability databases?Yes, the new version of the DSS-X core does not include the option for the attack. And it is pretty forward for users of the version 1 to avoid these probems. Just reject the 'inline XML' data transfer option.
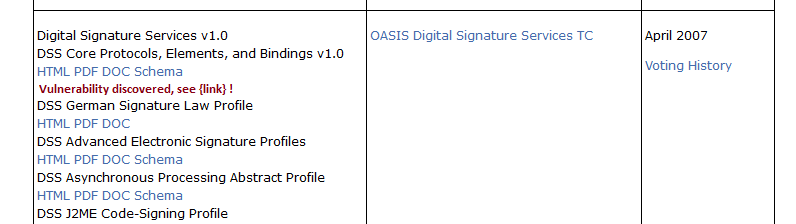
I thought of a warning iin the download section loke this
and a corresponding hint on the TC home page.
The vulnerability has the identifier CVE-2020-13101 assigned.
Greetings,
Andreas
/chet On Sun, May 17, 2020 at 12:46 PM Andreas Kuehne <kuehne@trustable.de> wrote:Hi Chet, we already discussed the topic soe time ago: The DSS core V1.0 has a vulnerability and we like to file it officially. Is there an official OASIS process for it? If not, I would suggest that we add a remark including the link to the explaination & mitigation document and the CVE at a prominent place on the TC home page and at the standards download section. Gretings, Andreas -- Andreas KÃhne Chair of OASIS DSS-X phone: +49 177 293 24 97 mailto: kuehne@trustable.de Trustable Ltd. Niederlassung Deutschland Gartenheimstr. 39C - 30659 Hannover Amtsgericht Hannover HRB 212612 Director Andreas KÃhne Company UK Company No: 5218868 Registered in England and Wales
-- Andreas KÃhne Chair of OASIS DSS-X phone: +49 177 293 24 97 mailto: kuehne@trustable.de Trustable Ltd. Niederlassung Deutschland Gartenheimstr. 39C - 30659 Hannover Amtsgericht Hannover HRB 212612 Director Andreas KÃhne Company UK Company No: 5218868 Registered in England and Wales