Superb!
I look forward to talking in person. Perhaps more than once.
tc
From: Shawn Riley <shawn.p.riley@darklight.ai>
Sent: Monday, April 29, 2019 10:11 AM
To: Considine, Toby <Toby.Considine@unc.edu>; openc2-lang@lists.oasis-open.org
Subject: RE: ISO 15926 for Cybersecurity
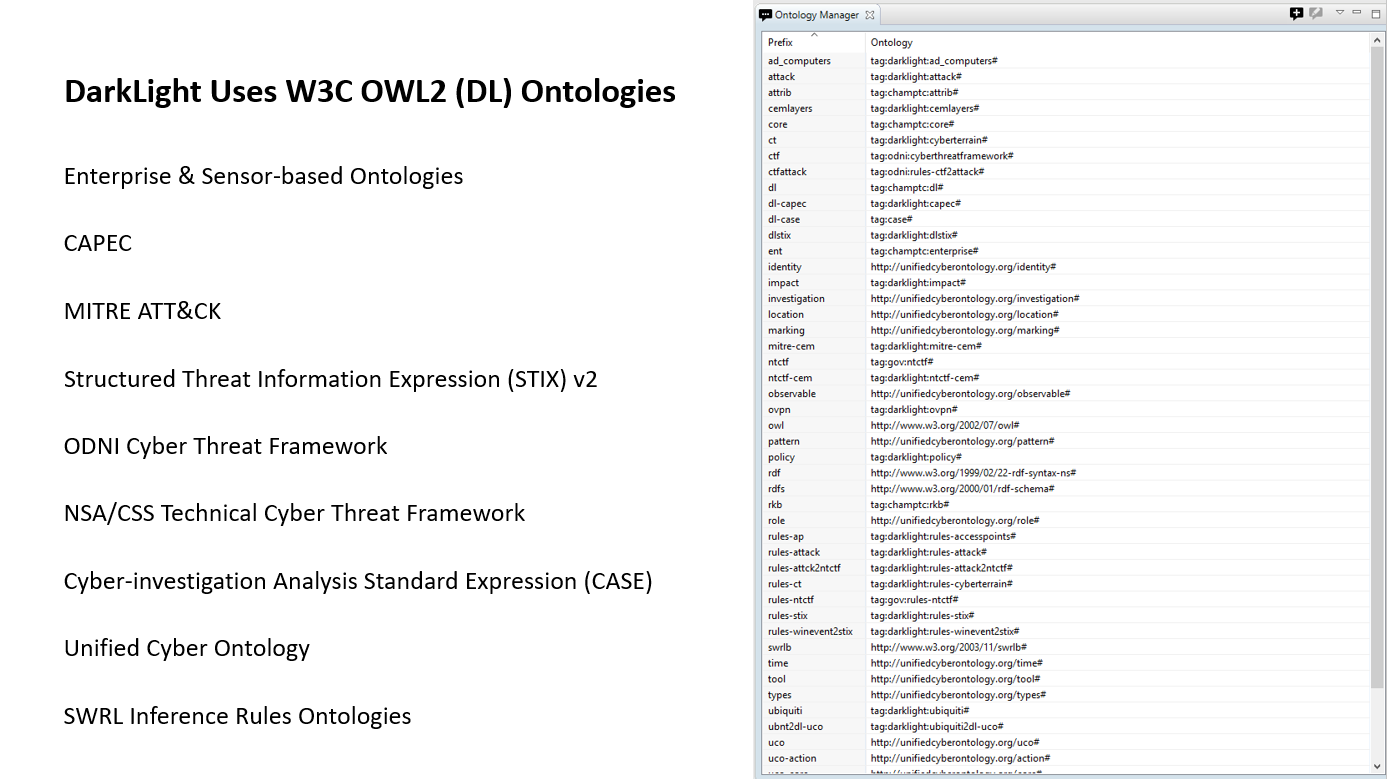
At Integrated Cyber on May 2-3 I’ll be giving a joint presentation with R9B on Modern A.I. Expert Systems for Active Defense and explaining how the expert system uses W3C OWL2 (DL) standardized knowledge representation language to create
ontologies. We have ontologies to represent enterprise assets, sensor output, ontologies to represent the layers of cyber terrain, ontologies to represent the cyber effects matrix (CEM), ontologies for cyber dictionaries like CAPEC, CWE, and CVE, ontologies
for modeling threats like STIX v2, ODNI Cyber Threat Framework, and the NSA/CSS Technical Cyber Threat Framework. We also have ontologies that are being developed by the wider cybersecurity community such as the Unified Cyber Ontology and the Cyber-investigation
Analysis Standard _expression_ (developed by the DFIR community). We also have SWRL ontologies that encode human expert experience in reasoning that can be applied to any knowledge in the knowledge base such as rules for reasoning over STIX data, rules for reasoning
over the NSA/CSS Technical Cyber Threat Framework, rules for converting sensor observations to STIX, rules for reasoning over the layers of the cyber terrain, etc.
Happy to chat more about ontologies (knowledge representation and reasoning) and how we’re using them in the cyber domain. If you’re at Integrated Cyber this week we can chat in person, otherwise we can find a time to chat online.
Best,
Shawn
Shawn Riley
Chief Visionary Officer &
Technical Advisor to the CEO
DarkLight, Inc.
Email:
shawn@darklight.ai

From:
openc2-lang@lists.oasis-open.org <openc2-lang@lists.oasis-open.org>
On Behalf Of Considine, Toby
Sent: Monday, April 29, 2019 7:47 AM
To: openc2-lang@lists.oasis-open.org
Subject: [openc2-lang] ISO 15926 for Cybersecurity
ISO 15926 for Cybersecurity
In large industrial controls systems have worked on ontological management for some time. For example, large oil and gas systems have multi-business unit scale control systems that have interactions with each other that vary from sequencing
(interfering with an upstream process will shutdown later sates in processing) to competition for resources over time, to spatial (these things run through the same chase, so a fire in one will shut down control of the other) and many more.
These large systems have built ontological systems around the processes to manage inter-system interactions and vulnerabilities. (I’m thinking of ISO 15926). Are there similar developments in use to understand cybersecurity issues in large
processes and should this sort of issue be noted in a high level view of distributed cybersecurity?
tc
"A designer knows he has achieved perfection not when there is nothing left to add, but when there is nothing left to take away."
-Antoine de Saint-Exupery
|
Toby Considine Toby.Considine@gmail.com |
|
Chair, OASIS OBIX Technical Committee Chair, OASIS WS-Calendar Technical Committee Editor, OASIS Energy Market Information Exchange (EMIX) Editor, OASIS Energy Interoperation |