This is a reminder of the upcoming OASIS Threat Actor Context – Technical Committee (TAC-TC) meeting upcoming on January 21 at 10:00 am EST.
https://www.oasis-open.org/apps/org/workgroup/tac/event.php?event_id=49808 An agenda for the meeting is forthcoming.
With the main point of this message out of the way, here is some additional food for thought:
As a knowledge engineer I have become extremely impressed with the cybersecurity experts in our community. The process of knowledge elicitation in this domain is much more pleasurable due to the maturity of our industry today compared to
just a few years ago. Looking over the list of members to this TC you can see the names of very knowledgeable people. I’m excited to see the work products I anticipate this group delivering. Each of us in this TC is a knowledge source that has a perspective
on what constitutes Threat Actor Context.
One of the many knowledge sources that addresses the context around Threat Actors is
NIST’s Special Publication 800-30, Guide for Conducting Risk Assessments. In this special publication is Appendix D - Threat Sources, it presents a taxonomy of threat sources inclusive
of adversarial threat sources. It calls out some basics. I’ve included a couple of excerpts below.
NIST’s taxonomy is just one example. Many of you have taxonomies you use when documenting the threat intelligence you have gathered. In recent threat intelligence reports about Threat Actors in the world news, there is information in the
narratives that I wish was expressed in a formal semantically interoperable standard format. If it were, these reports become useful beyond the human analyst, and could be interpreted by the growing number to intelligent systems.
I’d like to see so many questions machine queryable and the results machine readable.
- How is the adversary structured?
- Who, if any, are the adversary’s contracted resources?
- What is the adversary’s level of sophistication and maturity?
- What is the adversary’s strategy?
- What is the adversary’s typical motivation/intent?
- What are the adversary’s tactical habits?
Another knowledge resource that has relevancy is
The Organization Ontology. In my opinion being able to represent an adversary’s organizational structure is very helpful. When it comes to developing systems that represent organizational information, it makes sense to me to represent the adversary’s organization
with the same taxonomy as the defender’s organization. Sometimes the aggressor is a competitive organization.
From Appendix D of SP 800-30:
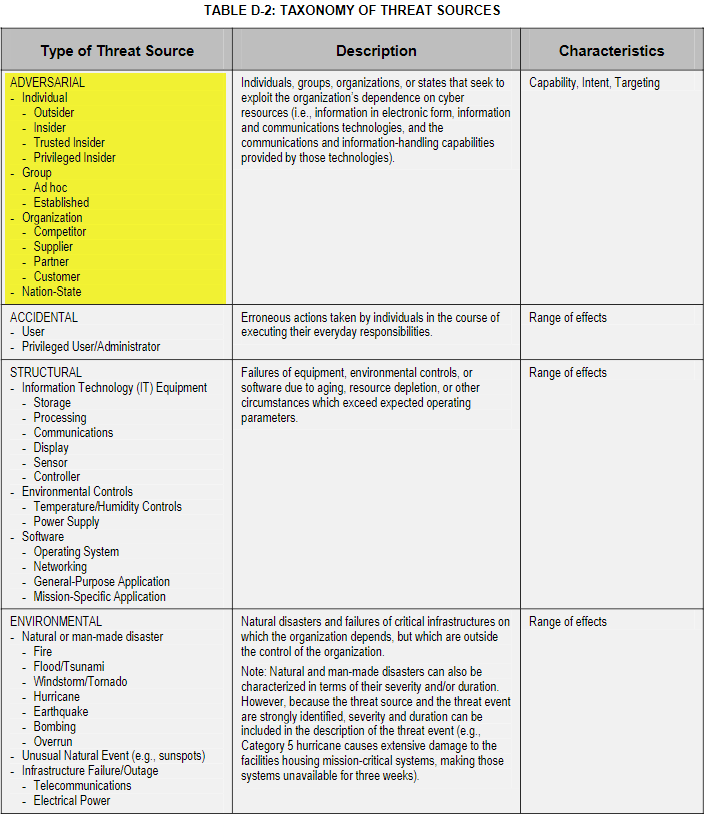
Context about adversary capability, intent, and targeting is given consideration and captured in assessment scales.

Looking forward to the meeting.
Regards,
Ryan E. Hohimer
CTO
DarkLight
Mobile: (509) 430-6890
710 George Washington Way, Suite A
Richland, Washington 99352
Email:
ryan@darklight.ai

This e-mail (including any attachments) may contain information that is private, confidential, or protected by attorney-client or other privilege. If you received
this e-mail in error, please delete it from your system without copying it and notify sender by reply e-mail so our records can be corrected.